AntiDDos

Effective protection
- Protect your network from large-scale attacks
- Protection of your business processes
- Protection against financial and reputational losses

Reliable, efficient operation
- Fast response time
- Automatic attack detection
- Elimination of the human factor
- High-performance operator platform

Simple service management
- Service management through the Client Portal
- Quick change of the protection scheme
- Online access to statistics and reports
- Incident notifications

Fast implementation
- Launch within 7 working days
- Dedicated team for the project

Predefined protection schemes
- 3 schemes with different sensitivity
- Thresholds determined by the bps and pps parameters for the target IP address
- Cleaning and filtering rules

Compatibility
- Initially works with such services as: Atman Cloud, Business Internet, Dedicated servers
What are DDoS attacks
and why are they so dangerous for you?
DDoS (Distributed Denial of Service) is an attack launched simultaneously from many computers and/or infected IoT devices (e.g., cameras) against the computer systems of content and Internet service providers. It is specific because it cannot be distinguished from normal traffic by classical security systems. Such an attack consists in saturating client resources (e.g., Internet connections) with requests, so for security purposes it is important to recognize and stop the attack at the level of the telecommunications operator’s infrastructure (e.g., Atman), which is able to receive and neutralize an attack that is potentially very dangerous for the end user of the service.
DDoS attacks have been around for a long time, but their form is becoming more and more advanced. Nowadays, such an attack can be ordered by anyone, because their availability and price are not an obstacle. It is one of the most common ways to maliciously block websites and web systems.
For an enterprise that provides online services, the losses associated with overloaded servers and access channels are not only limited to the inability to serve customers during an attack, but also lead to financial and reputational losses, loss of trust, or potential conflict within the organization. Protecting against DDoS attacks has become as important as protecting IT resources from hackers and computer viruses.
Infrastructure and operational model
The solution is based on hardware and software components. Hardware components include a sensor and a scrubber, which are installed in Atman data centers.
Anomaly response – a filter is launched and the traffic of the attacked host is redirected to the scrubber to mitigate the DDoS attack. The filtered traffic is sent back to the client through its main channel.
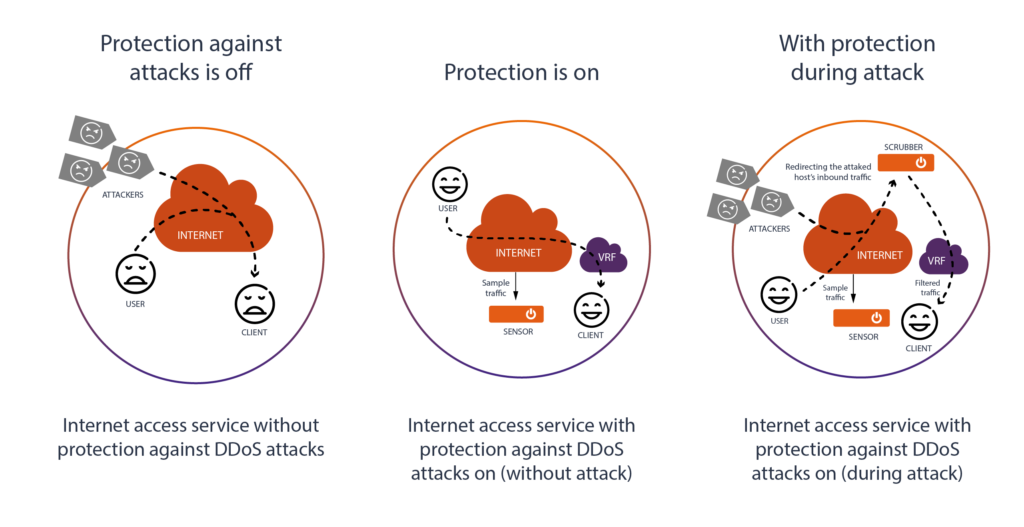
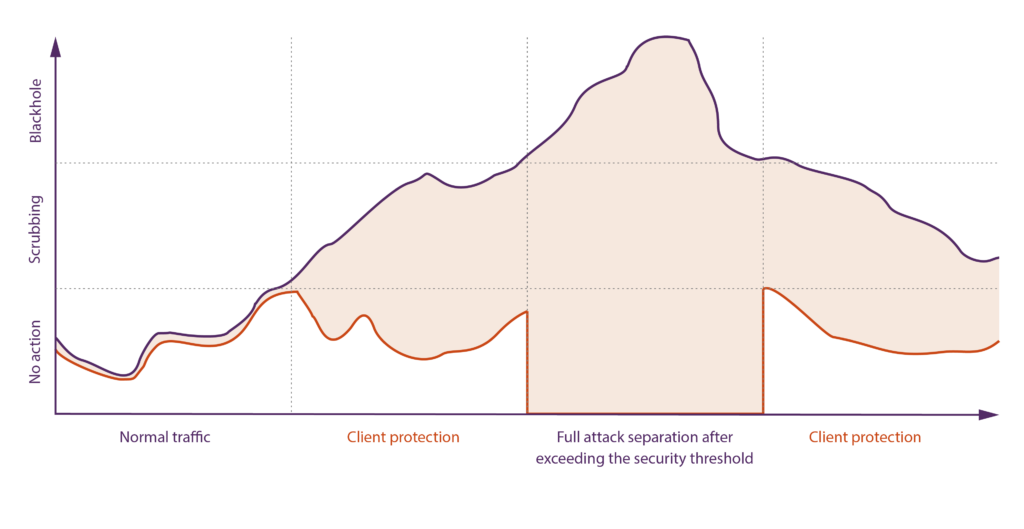
If the security thresholds are exceeded, the operator can activate a black hole to ensure that the client’s infrastructure is 100% separated from the sources of the attack.
 Cabinet
Cabinet